This article is a reproduction of a standard Steadfast Networks welcome email sent to new dedicated server customers. If you have lost your welcome email, you can use this information as a reference for service features and addon services you are eligible to request.
NOTE: Please read this message completely, as it contains important information about your new service with Steadfast Networks.
== Server Details ==
Your IP addresses and login information are sent in this section.
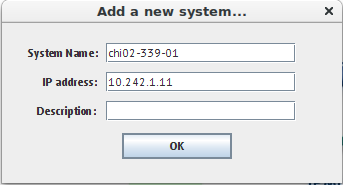
If included, your original email would indicate whether your server provides IPMI management and access to our Internal Network. The presence of IP addresses on your device entries at https://manage.steadfast.net will also confirm whether these features are available on your server.
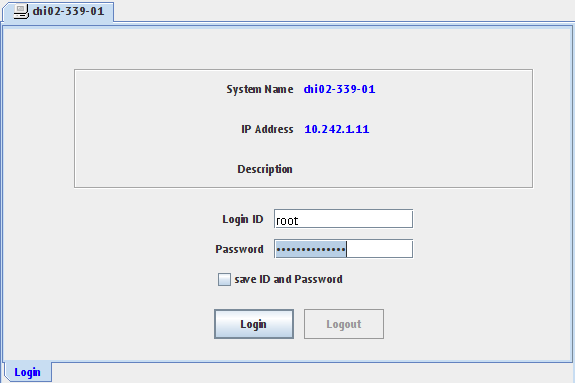
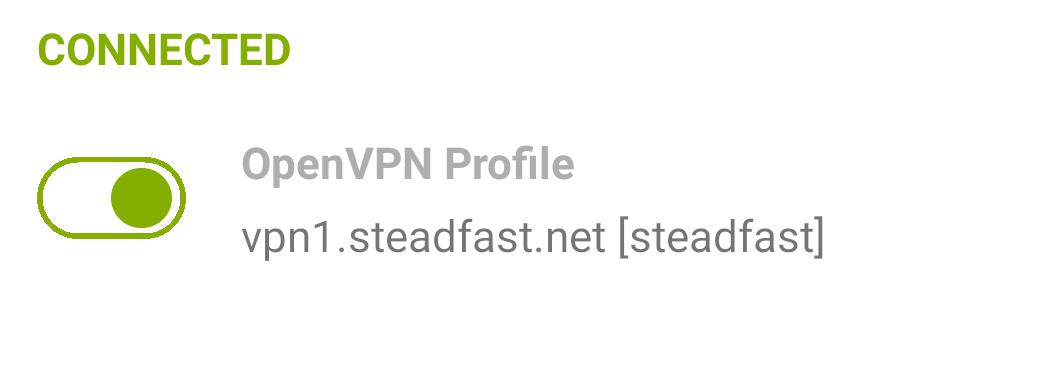
To access IPMI, you must use the Internal Network VPN service described below. Once connected, you can access IPMI with the provided details.
The Internal Network allows you to communicate with your other servers and the Steadfast SAN privately and unmetered. If you have a backup account with us, you can use the Internal Network to avoid charges for bandwidth used to make backups. If you use the shell backup server (SFTP, FTP, or rsync), connect to int.shell01.backup.steadfast.net (10.2.255.10). If you are using Idera Server Backup, allow access from int.cdp01.backup.steadfast.net (10.2.255.11).
If you would like access to IPMI or the Internal Network via VPN, please contact support@steadfast.net to request a VPN key. The VPN is supported on Windows Vista and later, MacOS X 10.4 and later, Linux, and FreeBSD. VPN access is also available on devices powered by iOS 6 and later or Android 4.0 and later. Please see http://steadfast.net/support/kb/58 for more information.
== Requested Software ==
This section describes the login information for any control panels or additional software you requested in your initial order.
== Account Details ==
You can access our billing and account management interface at the following URL (or you can log in from the login box at the top of any page of our main site) using the information previously sent to you. Your client ID is your login.
URL: https://manage.steadfast.net
== Additional IP Addresses ==
Please note that unless otherwise requested, we have allocated only one IP address to your server. We strongly recommend against using the primary IPv4 address for public services in most cases. By using secondary IPs instead, your server may be easier to access in case of an attack against it. Additionally, if you desire to change between different server offerings in the future, the primary IPv4 address must be changed. Up to 8 additional IPs may be requested at no charge by sending an email to ips@steadfast.net. Secondary IPs beyond the first 8 can be ordered for an additional monthly fee as long as they can be properly justified according to ARIN rules.
The same process and conditions apply to additional IPv6 addresses for your server. Currently, IPv6 allocations are free, and the default is to assign a /64 (1.6x10^19 addresses) on request. We will reserve a /56 allocation which can be configured and routed for you later as needed. The only justification needed to reserve a /56 is simply a request for IPv6 connectivity. We are unable to furnish multiple /56 allocations until the first is efficiently allocated, and we cannot fulfill requests for diverse (discontiguous) allocations.
If you would like us change the reverse DNS entries for your IPs, please send an email to dns@steadfast.net.
Please note that due to the way we allocate IP addresses, all requests must be reviewed and processed by a network engineer. This means that these allocations are processed during a limited window of 9 AM to 7 PM, Monday through Friday. Most requests submitted over the weekend will not be handled until 9 AM on Monday morning. Our technicians cannot generally escalate requests to be processed over the weekend and cannot guarantee a response time on such requests. Be sure to submit your requests during the normal working hours for the department to ensure a fast response. Reverse DNS requests are processed 24/7, but may be lower priority than standard support requests.
== Remote Reboot ==
If your server ever stops responding, you can access "Reboot Control" under individual servers within your "Device Manager" in our management system. This will allow you to power cycle and reboot your server without the intervention of a technician. Please note that if your server is responding, you should reboot it via the operating system, so as not to cause any data loss.
== Server Monitoring ==
All Basic Management systems can have one system monitor per device. This can be a ping monitor, HTTP monitor, SSH monitor, etc. Outage notifications are emailed to the address of your choosing. Full Management customers can have an unlimited number of system monitors and notifications of outages are sent to our support department, along with any instructions you specify. If you would like a monitor to be set up, please email monitors@steadfast.net with the name or IP of the system(s) and service(s) you want monitored along with the email address that should be notified, if you have Basic Management, or the necessary instructions, if you have Full Management.
For any server with a hardware RAID array, we can also setup email monitoring to alert you, with basic management, or to alert us, with full management, regarding potential issues with your RAID array. This can help prevent catastrophic failures and is highly recommended. The RAID monitor will not count as a service monitor on your account and can be setup by emailing support@steadfast.net.
To protect the stability of your server and avoid interfering with your software configuration, we do not configure automatic or proactive updating by default. Please be sure to contact us if you would like us to turn on automatic installation of updates or have notification of updates sent to a particular address. This may require periodic reboot of your server. If your service is fully managed, you may have notifications sent to our support staff, so that we may take proactive action. If we are notified of an update that requires a reboot, we will contact you to schedule it.
== Remote Backup Service ==
We offer 10 GiB of backup space to all Basic Management customers and 50 GiB to Full Management customers at no additional charge. Idera Server Backup software is also available for an additional $10 a month per Basic Management system and is available for free with Full Management systems. To read about all the features included with the Idera Server Backup software or to see other available backup options go to http://steadfast.net/services/backup.php. To request your backup space, please submit an email to backup@steadfast.net from one of the authorized email addresses on your account specifying whether you want a standard SSH/FTP/rsync backup account or an Idera based account and we will create an account for you.
== Enterprise Spam Filtering ==
We offer access to an Enterprise Spam Filtering appliance to any customers that wish to use it. This service is included with Full Management, and is otherwise $29.95 per month per 250,000 messages for Basic Management or colocation customers. If you would like to have this service activated for your account, please send an email to spamfilter@steadfast.net listing the domains you would like to set up.
== Announcements and Maintenance ==
As many of our customers have expressed that they do not want to receive service notices to the primary contacts within their accounts, we do not notify customers of most routine maintenance and service changes via email. If you would like to be notified when we post an announcement, please visit the following link and enter your email address in the "Subscribe" box on the right side of the page:
https://support.steadfast.net/News/List
You can also click on the RSS icon on the news page to access an RSS feed of announcements via your favorite RSS reader. We also provide links to recent announcements and company blog posts on our front page if you prefer to check manually.
== Requesting Technical Support ==
For someone to request support on one of your systems, the email address, name, and phone number MUST be listed as one of the contacts on your account. Additional authorized contacts can be added by accessing our management system and clicking "Client Profile," then "View Profile," and then clicking edit at the top of the "Authorized Contacts" section. This is required for security purposes.
To improve support speeds and to improve your overall experience we strongly recommend that you enter the login information to your systems. This data can be entered in the "Device Manager." Under each device, click the "Edit" link for the "Device Metadata" section. This is extremely important if you have Full Management, since if this information is not kept on file and up-to-date we cannot properly implement proactive support services.
If you have any further support questions, please visit our help desk at https://support.steadfast.net, or email support@steadfast.net. Please be sure to list your server's primary IP address and as much detail as possible about your problem when requesting support to ensure faster service.
Thank you for your business!
 (New system) button from the toolbar:
(New system) button from the toolbar: